| Cybersecurity | |
| << TO BE UPDATED, PLEASE VISIT AGAIN >> | |
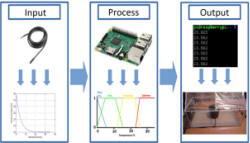
| My contribution in this area is the implementation of Spectral Clustering for anomaly detection in network traffic. This, because the exponential growth of network traffic has led to an increase in network anomalies such as: cyber attacks, network failures and hardware malfunctions. Detecting network anomalies is a critical task to maintain the security and stability of computer networks. Also, my expertise consists in detecting such anomalies, using support vector machine multi class, as a supervised algorithm to detect early, such anomalies in network traffic [1]. | |
| Some projects in this field where I have been working on: | |
| "Smart cybersecurity countermeasures for the network of the future."-CICERO | |
 [1]
Cicero website: Contramedidas inteligentes de ciberseguridad
para la red del futuro,
https://cicerocybersecurity.com/ceit-cicero
fortalecer-ciberseguridad-entornos-industriales/ [1]
Cicero website: Contramedidas inteligentes de ciberseguridad
para la red del futuro,
https://cicerocybersecurity.com/ceit-cicero
fortalecer-ciberseguridad-entornos-industriales/ |
The CICERO cluster aims to address
the positioning of its centers in Cervera 25 technology
related to Cybersecurity, concentrating this function on the
development of robust information processing systems to
identify and reduce system and network vulnerabilities,
based on the application of signal and data security
technologies, as well as the development of network
virtualization technologies and software-defined networks. The “Ayudas Cervera para Centros Tecnológicos 2023” programme of CDTI (Centre for the Development of Industrial Technology) under the Ministry of Science and Innovation , within the research project “CICERO– Contramedidas inteligentes de ciberseguridad para la red del futuro” with grant number CER-20231019. My contribution in this project has been focused on Detection of anomalies in the traffic network of Industrial Control Systems. |
|
|
|
|
Unsupervised detection system of Cyber-attack in the network traffic |
|
|
Spectral clustering is an unsupervised machine learning technique that involves grouping data points into clusters based on their similarity in a high-dimensional space. This approach involves first transforming the data points into a lower-dimensional space using a spectral embedding technique, which retains the most important features of the data. Next, a clustering algorithm is applied to the transformed data points to group them into clusters [2,3]. |
 Cicero website: Contramedidas inteligentes de ciberseguridad para la red del futuro, https://cicerocybersecurity.com [1] |
|
|
|
|
Cyber-attack detection in the network traffic |
|
|
The system “Cyber-attack detection in the network traffic by
supervised learning” uses commonly used machine learning
classification algorithms to solve the problem by
identifying the normal network traffics and attack classes
[2,3].
|
 Cicero website: Contramedidas inteligentes de ciberseguridad para la red del futuro, https://cicerocybersecurity.com [1,2,3] |
|
|
|
| References: | |
| [1] Contramedidas inteligentes de ciberseguridad para la red del futuro, https://cicerocybersecurity.com/ceit-cicero-fortalecer-ciberseguridad-entornos-industriales/ | |
| [2] 1st progress report of the “CICERO– Contramedidas inteligentes de ciberseguridad para la red del futuro” with grant number CER-20231019 | |
| [3] 2nd progress report of the “CICERO– Contramedidas inteligentes de ciberseguridad para la red del futuro” with grant number CER-20231019 | |
 |
Research Group |
 |
|
Mechatronics, Signal Processing, Control and Artificial Neural Networks |
||
| Department of
Information and communications technologies Technological Centre Ceit /“Researching Today, Creating the Future” |
||